Chances are that you or someone you know have been the victim of debit/credit card fraud. Even though your personal card is covered for any fraud and you have zero liability for any charges, having to go through the process of identifying and returning fraud charges and then being without a card while you wait for a new one (which has a whole new number) is frustrating and, let’s be honest, annoying. So how do these large scale debit card compromises keep happening? Today we will break down what has become the most popular method in recent years, which involves a party using illicit means to obtain huge lists of debit cards.
The relationship on how your money moves from your financial institution (FI) to the store you are shopping at is illustrated below. You are a customer of both that merchant, and the financial institution, but in most cases there is no direct link between the merchant and the FI. This is where the role of a third party payment processor comes into play. Very large merchants may use their own in-house payment processing, but for the majority of merchants this is handled by a third party. This company acts as the facilitator for the merchant to handle sending the payment request to the FI, which verifies the funds are available and then releases them to go back to the payment processor to be transferred to the merchant.
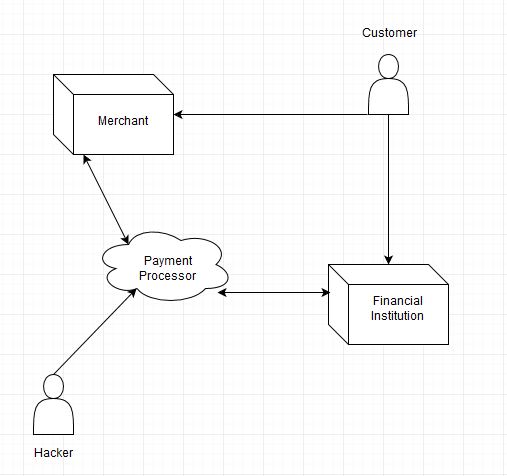
Enter a hacker or other ‘bad guy’. Using means such as hacking into a payment processor’s database to extract huge lists of stored debit card numbers or installing malware to the payment processor software system which then relays cards automatically, this individual or entity is able to obtain essentially all debit card numbers used within a certain timeframe. Depending on the size of the merchant, you can imagine the sheer volume of card numbers that can be obtained.
In this situation, there was nothing that the customer or financial institution could have done differently to prevent fraud charges from being ran through on the customer’s card. It happened because at one point the customer’s card was stored by a third party that the customer never interacted with directly and the financial institution simply approved the transaction to.
We hope this has helped to shed light on something that has become something of a recent epidemic in the financial sphere, illustrated why multiple breaches keep cropping up, and shows the importance of information security on not just the customer’s end, but for all parties involved in handling financial information.